Managing Cybersecurity Risks
Tristan Hunter and Deaglan Gahan share some of the strategies to prevent and mitigate cybersecurity breaches
DIGITALISATION is now ubiquitous across most projects and roles that chemical engineers fulfil. Supervisory control systems and big data analytics improve resource efficiency and reduce waste, while remote monitoring promotes safe and reliable operation of process equipment. Unfortunately, the increased adoption and complexity of digital solutions also leads to increased risk, much of which is invisible to an untrained eye. A recent survey of global CEOs found that cyber risks are seen by respondents as the largest threat to their organisation’s growth1.
Chemical engineers are often the protagonists in the process safety journey, and it’s therefore essential that they’re aware of potential cybersecurity risks and can question whether proportionate controls are in place. In this seventh article in the DigiTAG series, preventative and reactive strategies to managing cyber risk are explored to safeguard personal and commercial data, and the process itself.
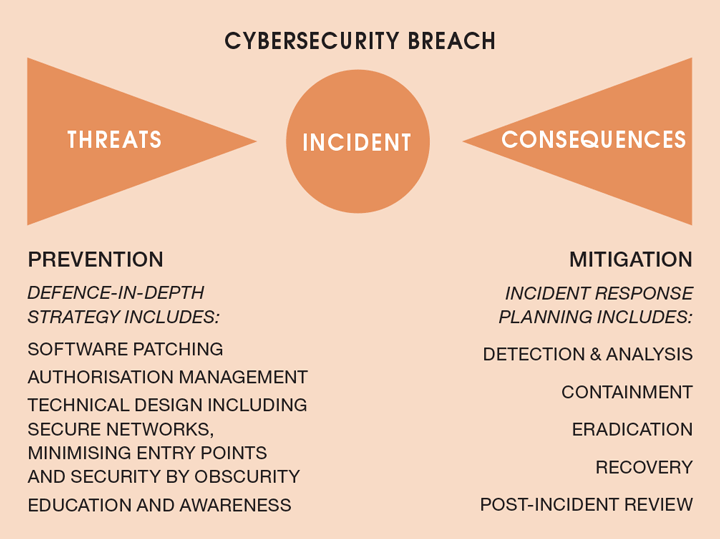
Previous articles in The Chemical Engineer have drawn parallels between cybersecurity and process safety (see TCE 983 p41). We continue this theme by introducing the concept of an operational technology (OT) cybersecurity risk bowtie diagram to illustrate two important tools for managing cybersecurity risks: defence-in-depth strategies and incident response plans.
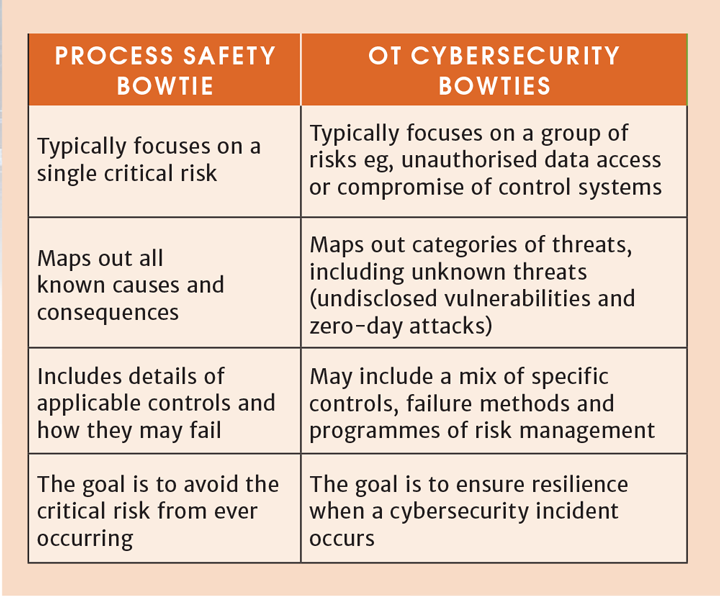
It’s important to acknowledge some key differences between a traditional critical risk bowtie and a cybersecurity bowtie (Table 1). These differences are due to the level of complexity and interconnectedness of OT systems.
Chemical engineers are often the protagonists in the process safety journey, and it’s therefore essential that they’re aware of potential cybersecurity risks

The defence in depth strategy
The term “defence-in-depth”, which exemplifies the preventative control on the left of the cybersecurity bowtie, describes a combination of cybersecurity controls used to protect digital systems from attackers. Analogous to process safety, defence-in-depth strategies employ multiple layers of protection to prevent and mitigate known risks. A control may also be implemented more than once – for example, a user may be required to provide a valid username and strong password to remotely connect to a virtual private network (VPN) and then need to authenticate a second time to access applications themselves.
The role of patching
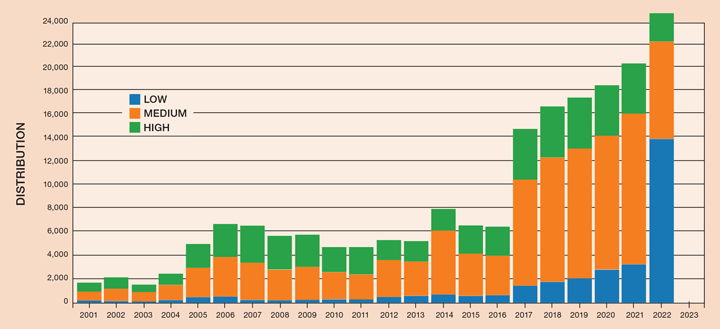
Cybersecurity breaches affecting consumers are increasingly making headline news. Often, the first piece of advice offered is to regularly “patch” your systems. The terminology can vary, but typically “patching” (or “updating”) refers to small, highly-targeted changes to computer software to fix functional or security issues. In contrast, “upgrades” are larger changes which may add new features or remove unmaintained functionality. Periodic and reactive patching should be performed frequently to minimise the time exposed to known vulnerabilities. Patching is becoming increasingly important as the number of known vulnerabilities continues to climb (Figure 2).
Patching usually requires restarting the device. However, organising a system outage or planned downtime can be challenging in some facilities. Sometimes this is not possible and known vulnerabilities must be managed over extended periods. Other vulnerabilities cannot be patched at all and risks must be managed for the remainder of an asset’s lifecycle. Vulnerable systems or equipment may be protected by improving the security of related hardware or software components. Other strategies include disabling remote access or removing legacy items from the operational network and configuring them to operate alone.
It’s therefore important that technical teams managing OT assets are aware of new vulnerabilities so they can assess and patch them, or otherwise respond appropriately. The Cybersecurity and Infrastructure Security Agency (CISA) publishes alerts and advisories in conjunction with vendors outlining the issue and potential remediations, and giving a risk score. It’s worthwhile ensuring someone monitors these alerts and escalates significant new risks through appropriate channels.
Vendors provide patches for supported software. However, some OT systems have a working lifespan of 20+ years and will remain in service well after the vendor has ceased updating. This obsolescence is becoming a driver for system upgrades across organisations since it’s sometimes the only way to remove legacy system vulnerabilities.
Compatibility of patches with connected systems is also a consideration. For example, the software that displays operator graphics in a control room must be compatible with that workstation’s operating system and other applications, such as anti-virus and disaster recovery and safety systems. Vendors sometimes offer patch validation services to confirm compatibility of third-party patches with their own software. It’s important to test changes in a controlled manner before deploying across an entire facility or organisation, even if there are no known or tested compatibility issues. Any patching should be performed under change management with sufficient testing and rollback planning beforehand, and system performance verification afterwards.
Regularly patching reduces but does not eliminate cybersecurity risks, as staff and vendors can only address vulnerabilities they know about. Attackers who discover a vulnerability are unlikely to inform vendors and instead use this knowledge to compromise systems that are believed to be secure. These “zero day” attacks can be difficult to combat. The “layers of protection” approach is therefore the best way to maximise system resilience.

Recent Editions
Catch up on the latest news, views and jobs from The Chemical Engineer. Below are the four latest issues. View a wider selection of the archive from within the Magazine section of this site.